- A Beginner’s Guide: Private and Public Key Cryptography Deciphered
- What is a Private Key?
- What is a Public Key?
- How are Public Keys generated?
- How does this provide security?
- Let’s do an Experiment
- The Discrete Log Problem
- Conclusion
- How to Generate a Bitcoin Address — Step by Step
- Introduction
- Dependencies
- Cryptography Primer
- Public Key Cryptography
- Creating a Bitcoin Address
- Private Key Generation
- Public Key Generation
- Compressed Public Key
- Address Generation
- Pay-to-Script Hash
A Beginner’s Guide: Private and Public Key Cryptography Deciphered
This article will explain at a high-level Private and Public Key Cryptography used in Bitcoin and it’s unique security feature.
We will be looking at how Public Keys are generated, why this is secure and how Private Keys are linked to Public Keys.
- Provide a high-level, easy to digest explanation of a complex topic
- Greater insight and understanding on how Bitcoin derives some of its security features
- By generating a Public Key, we have a way to interact with other people on the network openly, for example we may have some Bitcoin “ attached” to our Public Key
- The only way for us to prove that we own that Bitcoin is to prove that the Public Key was derived from our Private Key (by providing a signature, beyond the scope of this article)
What is a Private Key?
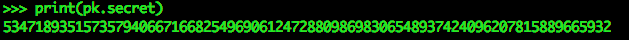
- A private key, is simply an extremely large and highly random number
- The image below shows a Private Key generated by a wallet program written by me
- DO NOT USE THIS NUMBER AS YOUR PRIVATE KEY
What is a Public Key?
- Public Keys can be shared with other people on the network
- We can generate addresses from the Public Key
- Public Keys are used by other users on the network to challenge ownership of Bitcoins
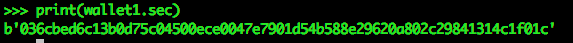
- This is a generated Public Key from our Private Key above
How are Public Keys generated?
- From a Private Key we can generate a Public Key
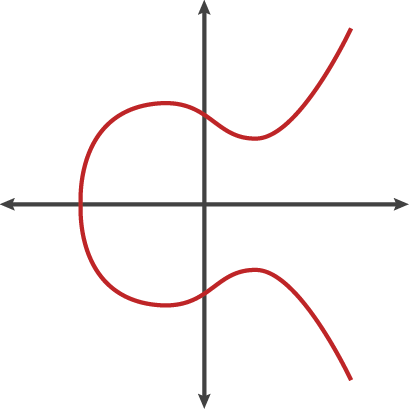
- The Public Key is an ( x ,y) co-ordinate on an Elliptic Curve
- The Public Key would be any point on this curve
- The Private Key is used as a scalar (A ll this means is that Private Key Number is used as a multiplier)
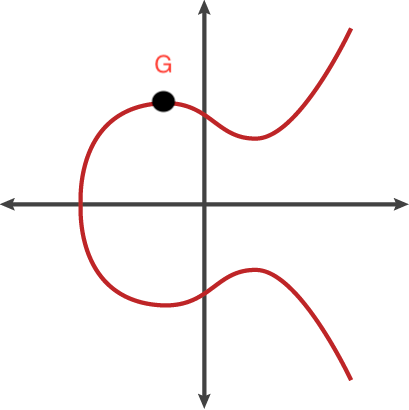
- All we need to know for now, is that there is a publicly known point on this curve, lets call it G
- G will be our starting position and has an ( x, y) co-ordinate
- What we do next is multiply the ( x, y) co-ordinate G, by itself Private Key (number) of times
- In other words, we are performing G*G, Private Key number of times
- When this occurs, there is a “ pin ball ” effect, this point G will bounce around the Elliptic Curve, like in a pin ball machine, hitting another point on the curve, reflecting over the x-axis and this is repeated * Private Key (number) of times
- Once this process is complete, we have our Public Key, viola!
- Our Public Key is nothing more than a ( x, y) co-ordinate on a curve
How does this provide security?
- Ok so we’ve simplified some complex topics
- For a more detailed look at Elliptic Curves and the Mathematics behind them here is a link to my next article Watch this space for a new article>
- The only way our Public Key, therefore our Bitcoin can be comprised is by revealing our Private Key
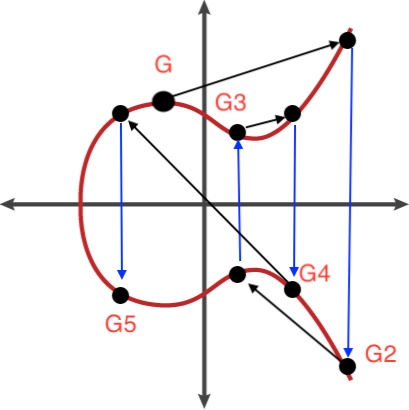
Let’s do an Experiment
- In the image below, we can see a billiards table and the starting position of the cue ball
- Lets say this starting position is our point G on the Elliptic Curve
- After knocking the cue ball around the billiards table we stop at our final position
- Let’s say this final position is our ( x, y) position on the Elliptic Curve, making it our Public Key
- I have video evidence… (Yes I did spend time knocking that cue ball around)
The Discrete Log Problem
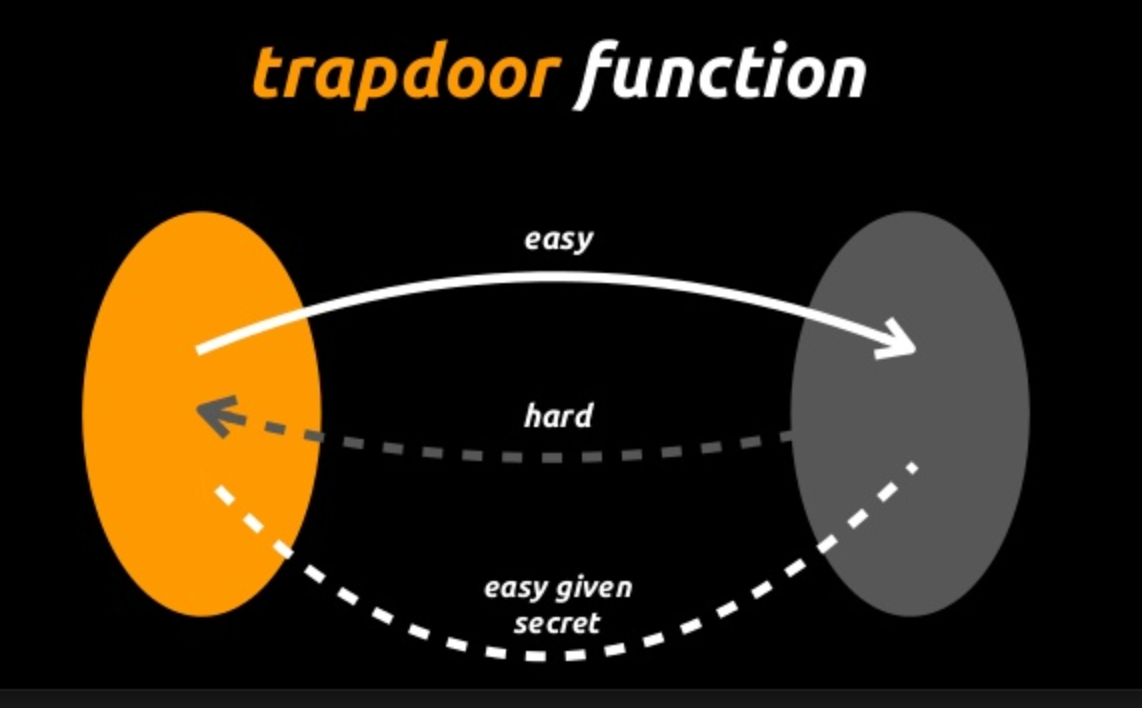
- Using the experiment above, we can demonstrate a key security feature of Private and Public Key Cryptography known as The Discrete Log Problem
- By knowing the starting position ( G) and the final position ( Public Key) we cannot deduce the scalar ( Private Key), given we are dealing with extremely large numbers
- This equation cannot be reversed, also known as a Trap-Door Function or a One Way Function, given publicly known information
- It’s easy to create the Public Key given the Private Key
- But it’s extremely difficult to calculate the Private Key from the Public Key
Conclusion
- Private keys are simply extremely large and random numbers
- Public Keys are ( x, y) points on an Elliptic Curve, generated by using the Private Key as a scalar
- Private and Public Key cryptography derives its security from the Discrete Log Problem, given the starting value and the end value, it’s difficult to deduce the scalar (Private Key)
- Trap-Door Functions are functions that cannot be reversed, it’s easy to create the Public Key given the Private Key but extremely difficult to calculate the Private Key from the Public Key
I highly recommend this course to any programmer serious about cutting their teeth into Bitcoin and Blockchain Technology (Not for the faint of heart)
Источник
How to Generate a Bitcoin Address — Step by Step
Here is a bash script that does what is outlined below: https://bit.ly/2MIgeOD
Introduction
This is a hands-on, technical guide about the generation of Bitcoin addresses including private and public keys, and the cryptography involved.
Learn more and join people in 22 countries around the world in my course on how to Become a Bitcoin + Blockchain Programmer.
This guide will walk you through all the steps to generate a Bitcoin address using the command line on a Mac. Similar steps should be possible on other operating systems using similar cryptographic tools. Lines starting with $ denote terminal commands, which you can type and run (without the $ of course).
Dependencies
- brew — Installation: https://brew.sh/
- pip — Installation: sudo easy_install pip
- libressl — Installation: brew install libressl
- base58 — Installation: pip install base58
Note: To do the contained openssl cli commands, I installed libressl in order for some of the elliptic curve commands to work as the current version of openssl cli on mac has a bug.
Cryptography Primer
Public Key Cryptography
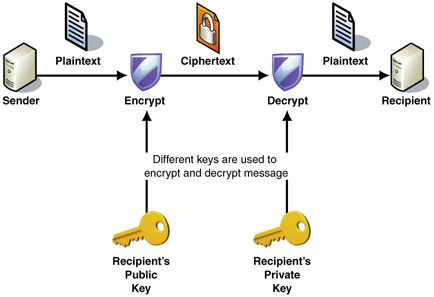
Or asymmetric cryptography, is a type of cryptography that uses key pairs, each of which is unique. The pair of keys includes a public key and a private key. This is the type of cryptography that Bitcoin uses to control funds. A public key can be generated from a private key, but not vice-versa (computationally too difficult). Also, something encrypted with a private key can be decrypted with the public key, and vice-versa, hence they are asymmetric.
- Encryption: When a user has a public key, a message can be encrypted using a public key, which can only be read by the person with the private key. This also works in reverse.
- Digital Signatures: A user can, with their private key and a hash of some data, use a digital signature algorithm such as ECDSA, to calculate a digital signature. Then, another user can use the algorithm to verify that signature using the public key and the hash of the same data. If it passes, this proves a user did in fact submit a specific message, which has not been tampered with.
- Digital Fingerprint: Is a way to represent an arbitrarily large data set by computing the hash of it to generate a fingerprint of a standard size. This fingerprint would be so difficult to replicate without the same exact data, which can be assumed to have not been tampered with.
Private keys are what prove you can send Bitcoin that has been sent to you. It is like the password to your bank account. If you lose it or someone else gets a hold of it, you’re toast.
Public keys help people know how to send you Bitcoin.
Creating a Bitcoin Address
Private Key Generation
Private keys can be any 256 bit (32 byte) value from 0x1 to 0xFFFF FFFF FFFF FFFF FFFF FFFF FFFF FFFF BAAE DCE6 AF48 A03B BFD2 5E8C D036 4140 .¹
The total possible number of private keys is therefore 2²⁵⁶ or 1.16 x 10⁷⁷. Imagine the total number of atoms in your body, then imagine that each of those atoms is an earth. The total number of atoms on all of those earths is about 7 x 10⁷⁷.² There is virtually no chance that your random private key will ever be generated randomly or found by someone else.
A common (but not the most secure) way of creating a private key is to start with a seed, such as a group of words or passphrases picked at random. This seed is then passed through the SHA256 algorithm, which will always conveniently generate a 256 bit value. This is possible because every computer character is represented by an integer value (see ASCII and Unicode).
Note: SHA256 is a one-way, deterministic function meaning that it is easy to compute in one direction, but you cannot reverse it. In order to find a specific output, you have to try all the possible inputs until you get the desired output (brute forcing) and it will always produce the same output given the same input, respectively.
The seed can be used to generate the same private key if the same hashing algorithm is used in the future, so it is only necessary to save the seed.
This private key is in hexadecimal or base 16. Every 2 digits represents 8 bits or 1 byte. So, with 64 characters, there are 256 bits total.
Public Key Generation
Public keys are generated from the private keys in Bitcoin using elliptic curve ( secp256k1 ) multiplication using the formula K = k * G , where K is the public key, k is the private key, and G is a constant called the Generator Point⁴, which for secp256k1 is equal to:
It doesn’t seem to be known how this point was chosen by they designers of the curve. Also, this algorithm is a one-way algorithm, or a “trap door” function so that a private key cannot be derived from the public key. It is important to note that elliptic curve multiplication is not the same as scalar multiplication, though it does share similar properties.
To do this in the terminal from our private key earlier,
This public key contains a prefix 0x04 and the x and y coordinates on the elliptic curve secp256k1 , respectively.
Compressed Public Key
Most wallets and nodes implement compressed public key as a default format because it is half as big as an uncompressed key, saving blockchain space. To convert from an uncompressed public key to a compressed public key, you can omit the y value because the y value can be solved for using the equation of the elliptic curve: y² = x³ + 7. Since the equation solves for y², the right side of the equation could be either positive or negative. So, 0x02 is prepended for positive y values, and 0x03 is prepended for negative ones. If the last binary digit of the y coordinate is 0, then the number is even, which corresponds to positive. If it is 1, then it is negative. The compressed version of the public key becomes:
The prefix is 0x02 because the y coordinate ends in 0xa4 , which is even, therefore positive.
Address Generation
There are multiple Bitcoin address types, currently P2SH or pay-to-script hash is the default for most wallets. P2PKH was the predecessor and stands for Pay to Public Key Hash. Scripts give you more functionality, which is one reason why they are more popular. We’ll first generate a P2PKH original format address, followed by the now standard P2SH .
The public key from the previous output is hashed first using sha256 and then hashed using ripemd160 . This shortens the number of output bytes and ensures that in case there is some unforeseen relationship between elliptic curve and sha256, another unrelated hash function would significantly increase the difficulty of reversing the operation:
Note that since the input is a string, the xxd -r -p will convert the hex string into binary and then output it in hexdump style (ascii), which is what the openssl hashing functions expect as input.
Now that we have hashed the public key, we now perform base58check encoding. Base58check allows the hash to be displayed in a more compact way (using more letters of the alphabet) while avoiding characters that could be confused with each other such as 0 and O where a typo could result in your losing your funds. A checksum is applied to make sure the address was transmitted correctly without any data corruption such as mistyping the address.
Bitcoin P2PKH addresses begin with the version byte value 0x00 denoting the address type and end with a 4 byte checksum. First we prepend the version byte (prefix) to our public key hash and calculate and append the checksum before we encode it using base58 :
Note: -c denotes a checksum is to be applied. The checksum is calculated as checksum = SHA256(SHA256(prefix+data)) and only the first 4 bytes of the hash are appended to the end of the data.
The resulting value is a P2PKH address that can be used to receive Bitcoin: 16JrGhLx5bcBSA34kew9V6Mufa4aXhFe9X
Pay-to-Script Hash
The new default address type is a pay-to-script-hash, where instead of paying to a pubKey hash, it is a script hash. Bitcoin has a scripting language, you can read more about it here. Basically it allows for things like multiple signature requirements to send Bitcoin or a time delay before you are allowed to send funds, etc. A commonly used script is a P2WPKH (Pay to Witness Public Key Hash): OP_0 0x14
where the PubKey Hash is the RIPEMD160 of the SHA256 of the public key, as before, and 0x14 is the number of bytes in the PubKey Hash. So, to turn this script into an address, you simply apply BASE58CHECK to the RIPEMD160 of the SHA256 of the script OP_0 0x14
except you prepend 0x05 to the script hash instead of 0x00 to denote the address type is a P2SH address.
If you like the article, check out my course on how to Become a Bitcoin + Blockchain Programmer.
Источник