- Bitcoin stealer что это
- Bitcoin stealer script
- Лучшее Руководство по Биткойн-скриптам
- Введение в Биткойн-скрипт
- Тьюринг Неполный
- Так почему же Биткойн-скрипт Тьюринга не завершен?
- Обратная полировка
- На основе Стека
- Далее-Как
- Transaction Input
- Transaction Output
- Conditions of a transaction
- The bitcoin Script Transaction: Behind the Scenes
- A Closer Look at Transaction Outputs
- An Even Closer Look at Transaction Inputs
- Serialization of Transactions
- The Output Serialization
- The Input Serialization
- How Does the Script Work?
- Simple Addition Using Bitcoin Script with a Check
- Simple Duplication in the Script
- The Game of Locking and Unlocking
- Script Implementation of the Unlocking/Verification Process
- How does CHECKSIG work?
- Performing maths on the curve.
- Mathematical properties of an elliptical curve
- So how does signature verification work on the elliptical curves?
- What could go wrong in Elliptical curves?
- END OF PART 1
Bitcoin stealer что это
SIMILARITY MODE is the best version of our Crypto Stealer.
-it will replace any copied BTC/Coin address in clipboard with a SIMILAR/IDENTICAL address of yours.
Let’s be honest. When you deal with cryptocurrency, you will ALWAYS check the prefix/suffix of an address just to be sure that it’s correct when you Paste it. We all do that, do you agree?
But what if the address the user will Paste will look almost identical as the one he first copied? Like this:
1B EuePkQZF3e4uwZ1XZrKqaaeQ1Ryox ST7 — User COPIES this address
1B g3ZrS2NfF7XQ7BqowpPwnw25yboqw ST7 — But PASTES this address (yours)
This is what our Stealer does. Will trick the victim.
It will run in the background as a HIDDEN process and wait for the victim to use crypto. (BTC,ETH etc)
When the victim uses crypto and COPIES a BTC address, the stealer will detect, find match, and REPLACE the address he copied to an IDENTICAL address from your list.
This will result in tricking the victim and make him PASTE a wrong address and therefore, since the addresses look identical, the user won’t notice the change and make the payment to your address instead. Awesome, isn’t it?
Watch the Demonstration video above.
REQUIREMENTS — SIMILARITY MODE (click here)
You must generate 3 million Bitcoin addresses of your own in order for Similarity Mode to work. Why?
Because our Stealer needs to have a HUGE address list in which it would search & find matching addresses that look identical as the victim’s. The bigger the list, the better.
But don’t worry. They are easy to generate.
We will teach you how to generate them.
Also, you will generate the addresses locally on your PC along with their Private Keys. We don’t need your Private Keys.
Those are yours to keep. All we need from you is the list of the Public Keys so we can build the file for you.
Contact us for more info & help
Why choose Similarity Mode?
-High success rate since the addresses are identical.
-Will 100% trick the victim.
-Access to Online Logs Panel (will log used addresses)
-Private Key Stealer
-Anti-Taskmgr
-Video Tutorials & 24/7 Support
& many others
The program that generates the final .exe that contains your addresses
-You will be able to build UNLIMITED files in both Simple & Similarity Mode
Источник
Bitcoin stealer script
Цель этого руководства-помочь вам понять логику биткоин-скрипта. Так как будет слишком много. Чтобы охватить, руководство будет разделено на две части. Биткойн был создан только для одной цели…транзакций. Биткойн смог показать миру, что платежная система может существовать на децентрализованной одноранговой системе. Однако что происходит за кулисами этих сделок? За каждой маленькой транзакцией есть какой-то код. Работающий в фоновом режиме. Этот код является языком сценариев Биткойна или просто скриптом Биткойна для краткости.
Лучшее Руководство по Биткойн-скриптам
Введение в Биткойн-скрипт
Script-это подобный Forth. Основанный на стеке. Обратный польский. Неполный язык Тьюринга.
Да, это звучит очень сложно. Но на самом деле это не так. Давайте пройдемся по каждому члену с обратной стороны.
Тьюринг Неполный
Неполный язык Тьюринга будет иметь ограниченную функциональность и не будет способен совершать прыжки и/или циклы. Следовательно. Они не могут войти в бесконечный цикл. Быть полной программой Тьюринга означает. Что при наличии ресурсов и памяти полная программа Тьюринга сможет решить любую проблему. Солидность является примером полного языка Тьюринга.
Так почему же Биткойн-скрипт Тьюринга не завершен?
Потому что в этом нет необходимости. Биткойн-скрипт не должен быть таким сложным. Как смарт-контракт Ethereum. На самом деле. Если бы сценарий был полным по Тьюрингу. Он дал бы злоумышленникам свободу создавать сложные транзакции и съедать хэш-скорость сети Биткойнов и замедлять всю систему.
Обратная полировка
Обратная польская нотация-это система. В которой операторы следуют за операндами.
- 3+4 будет выглядеть как 34+.
- Итак, для более длинных более сложных сумм:
- 5*3+4 появится как 534+*.
На основе Стека
Стеки-одна из самых популярных структур данных. Согласно Викибукам, их можно логически представить как линейную структуру, представленную реальным физическим стеком или кучей, структурой. В которой вставка и удаление элементов происходят на одном конце. Называемом вершиной стека.
Основная идея стека-LIFO или Last In First Out. Рассмотрим следующую стопку книг:
Какая первая книга была положена в эту стопку? Одинокий Волк и детеныш, верно? Какая была последняя книга? Сады Луны.
Если кто-то возьмет книгу из этой стопки, то
Следовательно. Последний Вход-Первый Выход.
Последняя книга. Которая попала в эту стопку. Будет первой книгой. Которую вынут.
Теперь есть две операции стека. О которых вам нужно знать:
Толчок: Акт добавления вещей в стек называется толчком.
Pop: Акт удаления вещей из стека называется popping. Как уже упоминалось ранее. Последний элемент. Который был помещен в стек. Выскакивает первым.
Далее-Как
Это довольно прямолинейно. Биткойн-скрипт похож на язык программирования “Forth”. Который также основан на стеке.
Итак, теперь мы хотя бы знаем. Что такое скрипт. Давайте разберемся. Как работают транзакции.
Прежде чем мы продолжим. Огромное спасибо профессору Дональду Джею Паттерсону и его Youtube-каналу “djp3” за объяснение.
Предположим. Алиса хочет отправить Бобу определенное количество биткоинов. Как работает транзакционная система в биткойне? биткойн — транзакции сильно отличаются от транзакций с фиатными кошельками. Если бы Алиса дала Бобу 2 доллара. Она бы физически достала 2 доллара из своего бумажника и отдала их Бобу. Однако в биткойне все работает совсем не так . Вы физически не владеете никаким биткоином. Тоу вас есть. Является доказательством того. Что у вас есть биткоины.
Есть еще две вещи которые вы должны знать:
- Майнеры проверяют ваши транзакции. Помещая данные в шахты. Которые они заблокировали.
В обмен на предоставление этой услуги они взимают комиссию за транзакцию.
- When it comes to FIAT currency, you don’t really keep track of how and where you got that specific note from. Eg. Open your wallet right now and take out all the notes and coins in it. Can you tell where exactly did you get each and every specific note and coin from? Chances are that you don’t. However, in bitcoin, the history of each and every single bitcoin transaction is taken note of.
Ok, so now let’s do a deep dive into how a bitcoin transaction between Alice and Bob takes place. There are two sides to a transaction. The Input. And the Output. This entire Transaction will have a name that we will figure out in the end. For now, let’s look at the dynamics.
Transaction Input
In order to make this transaction happen. Alice needs to get bitcoins which she has received from various previous transactions. Remember, like we said before. In bitcoins, each and every coin is accounted for via a transaction history.
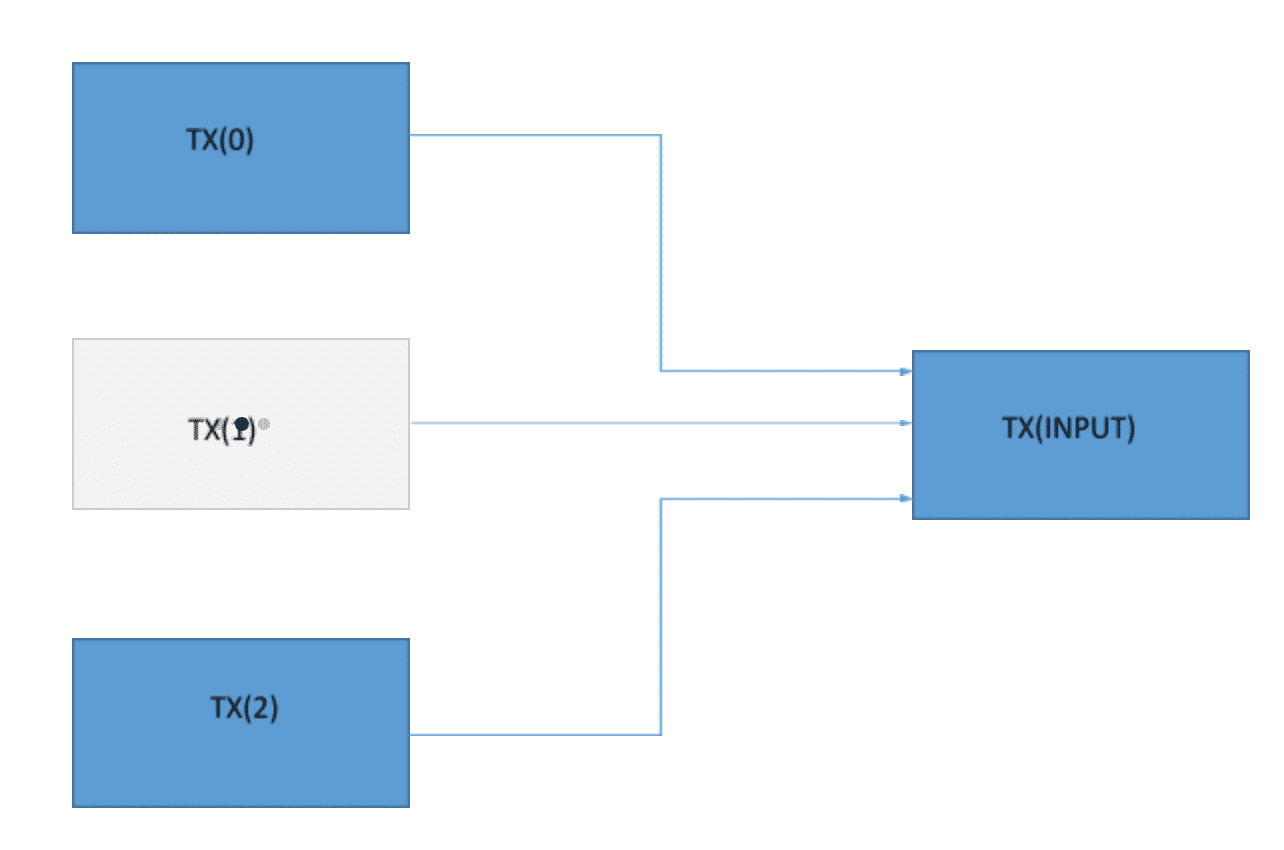
So, suppose Alice needs to pull bitcoins from the following transactions which we shall name TX(0). TX(1) and TX(2). These three transactions will be added together and that will give you the input transaction which we shall call TX(Input).
Diagrammatically. It will look like this:
So, that is it from the input side. Let’s check out what the output side will look like.
Transaction Output
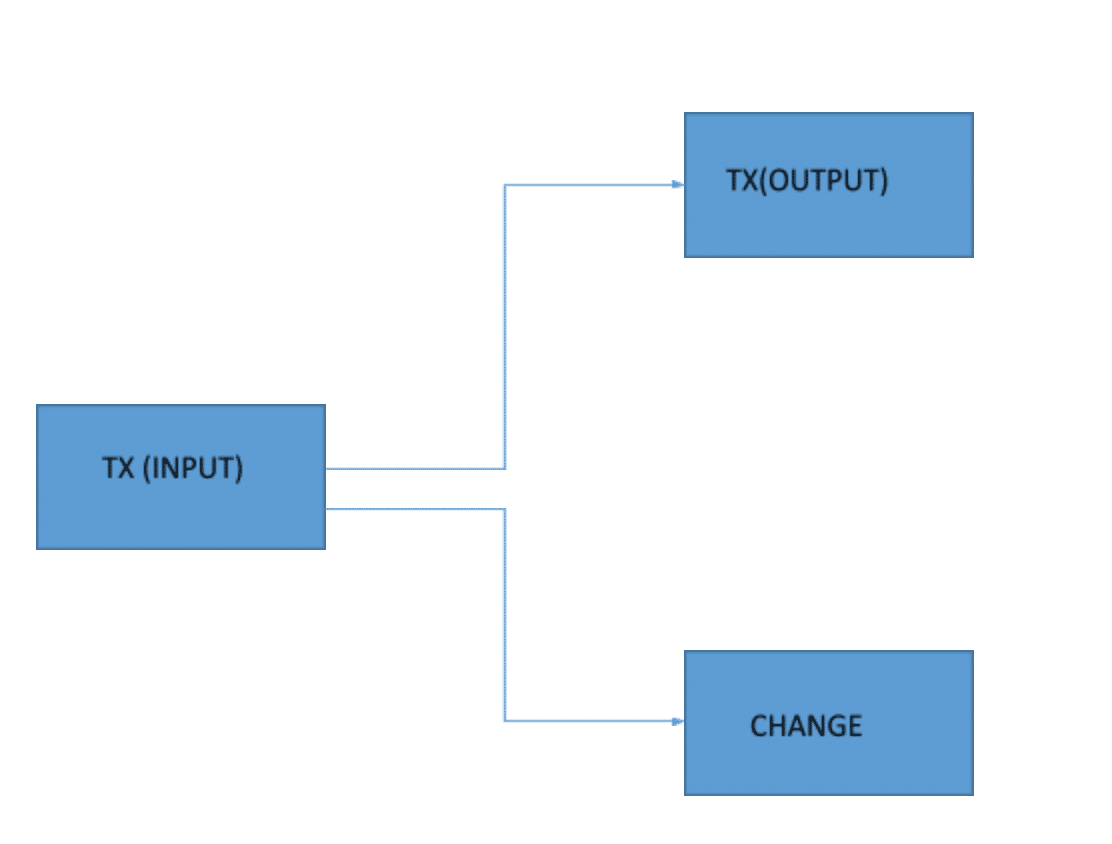
The output basically will have the number of bitcoins that Bob will possess, post-transaction and any remaining change that is left over. Which is then sent back to Alice. This change then becomes her input value for all future transactions.
A pictorial representation of the output side looks like this:
Now, this is a very simple transaction that has just one output (apart from the CHANGE). There are transactions that are possible with multiple outputs.
This is what the basic layout of the transaction looks like. For this entire thing to go through, however. Certain conditions must be met.
Conditions of a transaction
- TX(Input) > TX(output). The input transaction has to be always greater than the output transaction. In any transaction. The deficit between the input and the output (output+change) is the transaction fees that miners collect. So:
Transaction fees = TX(Input) – (TX(output) + Change).
- In the input side:
TX(0) + TX(1) + TX(2) = TX(Input).
If Alice doesn’t have the funds necessary to carry out the transactions then the miners will simply reject the transactions.
- Bob will have to show that he can provide the proof needed to get the bitcoins. Alice will lock the transactions with Bob’ public address. He will need to produce his private key to unlock the transactions and gain access to his fees.
- Alice also needs to verify that she has the required rights to send over the bitcoins in the first place. The way she does that is by signing off the transaction with her digital signature (aka her private key). Anyone can decode this by using her public key and verify that it was indeed Alice who sent over the data. This proof is called “Signature data”. Remember this because this will be very important later on.
So, what is going to be the name of this entire transaction?
The Input (including the signature data) and the output data is added together and hashed using the SHA 256 hashing algorithm. The output hash is the name that is given to this transaction.
So, now lets a look behind the scenes and see what the transaction actually looks like.
The bitcoin Script Transaction: Behind the Scenes
This is what the transaction looks like in the code form.
Suppose Alice wants to send 0.0015 BTC to Bob and in order to do so. She sends inputs which are worth 0.0015770 BTC. This is what the transaction detail looks like:
Image courtesy: djp3 youtube channel.
The first line you see:
Is the name of the Transaction aka the hash of the input and output value.
Vin_sz is the number of input data since Alice is sending the data using only one of her previous transactions, it is 1.
Vout_sz is 2 because the only outputs are Bob and the change.
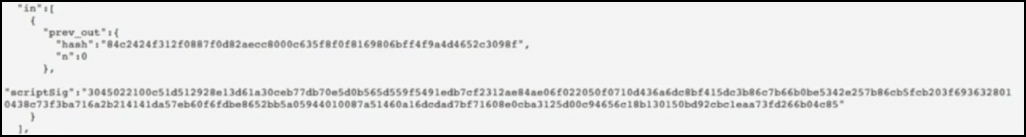
This is the Input data:
See the input data? Alice is only using one input transaction (in the example that we gave above. This will be TX(0)). This is the reason why vin_sz was 1.
Below the input data is her signature data.
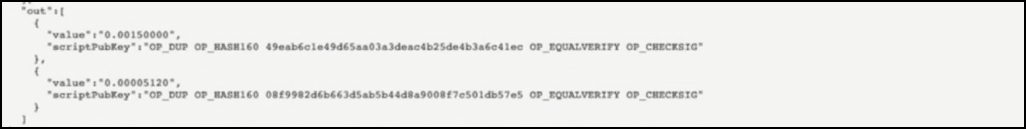
Underneath all this is the output data:
The first part of the data signifies that Bob is getting 0.0015 BTC.
The second part signifies that 0.00005120 BTC is what Alice is getting back as change.
Now, remember that out input data was 0.0015770 BTC? This is greater than (0.0015 + 0.00005120). The deficit of these two values is the transaction fee that the miners are collecting.
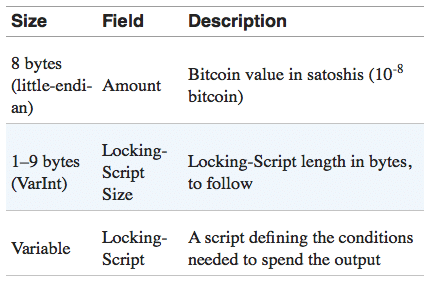
A Closer Look at Transaction Outputs
As we have seen above. Every input in a transaction turns into outputs. Some of these outputs are spent. While some are unspent and becomes change. This change is also known as UTXO or Unspent Transaction Output. UTXO goes on to become Inputs in future transactions.
Every transaction output consists of two parts:
- The value of that output.
- The cryptographic puzzle which either called a locking script. Or a witness script or a scriptPubKey. The puzzle needs to be unlocked in order to spend the money. This puzzle is coded using the bitcoin Script language.
So, let’s examine the outputs of a transaction to identify the above-mentioned parts in it. Code taken from Andreas M. Antonopoulos. “Mastering bitcoin.”
Alright. So we have two outputs in the code given above.
One output has a value of 0.015 BTC while the other has a value of 0.0845 BTC. In order to unlock the value of 0.015, the locking script that one needs to unlock goes like this:
“scriptPubKey”: “OP_DUP OP_HASH160 ab68025513c3dbd2f7b92a94e0581f5d50f654e7 OP_EQUALVERIFY OP_CHECKSIG”
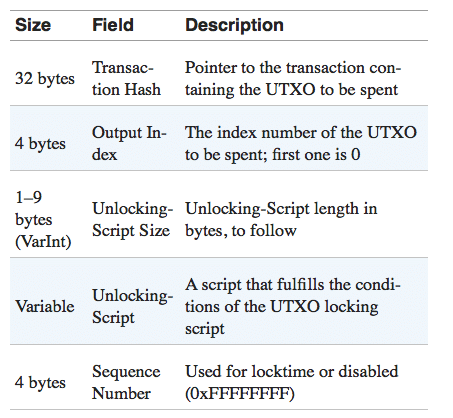
An Even Closer Look at Transaction Inputs
Now let’s looks at the other side of the coin. The transaction inputs.
In order to do an Input. The user’s wallet goes through their UTXOs and selects the ones which have enough value for the transaction to go through.
Eg. if Alice wants to send 0.15 BTC to Bob and here UTXO set looks like this:
Which UTXOs will be chosen for this transaction? That ‘s correct. A and B will be chosen. And whatever is left over will become the UTXO for Alice’s next transaction.
Now, let’s look at an input code.
Let’s see what each part of the input script includes:
- txid: The transaction ID refers the transaction from which this UTXO was generated. This helps keep track of the transaction
- vout: This refers to which output from that transaction is being used. Eg. if that transaction had two UTXOs the first one will be labeled 0(because as we have seen before. Counting starts from 0 and not 1) and the second one will be labeled 1. In this case. We are using the first UTXO i.e.UTXO 0.
- scriptSig: As we have mentioned before. Each UTXO contains a locking script. The scriptSig includes the data necessary to unlock the data.
- sequence: Was included to help people update their transactions before they are confirmed and finalized in a block. Not really that relevant to help understand the basics.
Serialization of Transactions
Now let’s bring of this together and see what we have. When a transaction is relayed over a network. They are serialized. As Andreas Antonopoulos says,
“Serialization is the process of converting the internal representation of a data structure into a format that can be transmitted one byte at a time. Also known as a byte stream.”
In the previous two sections. We saw a simple one input and one output transaction. if we were to serialize it and store it in hexadecimal format. What would it look like?
0100000001186f9f998a5aa6f048e51dd8419a14d8a0f1a8a2836dd73 4d2804fe65fa35779000000008b483045022100884d142d86652a3f47 ba4746ec719bbfbd040a570b1deccbb6498c75c4ae24cb02204b9f039 ff08df09cbe9f6addac960298cad530a863ea8f53982c09db8f6e3813 01410484ecc0d46f1918b30928fa0e4ed99f16a0fb4fde0735e7ade84 16ab9fe423cc5412336376789d172787ec3457eee41c04f4938de5cc1 7b4a10fa336a8d752adfffffffff0260e31600000000001976a914ab6 8025513c3dbd2f7b92a94e0581f5d50f654e788acd0ef800000000000 1976a9147f9b1a7fb68d60c536c2fd8aeaa53a8f3cc025a888ac 00000000
Yup, this author didn’t accidentally bang his head on the keyboard here… that’s what it actually looks like.
However, don’t get scared. We will make sense of it soon enough. Somewhere in that hexadecimal stream. We have out input data and our output data. Let’s find both of them!
The Output Serialization
The serialization of the output part of the transaction contains the following parts:
Image Credit: Andreas Antonopoulos “Mastering Bitcoin”
Now, what data about the output do we actually know?
- There are two output values.
- One output value is worth 0.015 BTC or 1,500,000 satoshis
- In hexadecimal 1,500,000 is 16 e3 60, which when coded in little-endian i.e. least significant byte first notation gives 60 e3 16.
- The scriptPubKey length is 25 bytes. Which is 19 in hexadecimal.
So, take note of these pieces of information. Let’s search for our output data.
0100000001186f9f998a5aa6f048e51dd8419a14d8a0f1a8a2836dd73 4d2804fe65fa35779000000008b483045022100884d142d86652a3f47 ba4746ec719bbfbd040a570b1deccbb6498c75c4ae24cb02204b9f039 ff08df09cbe9f6addac960298cad530a863ea8f53982c09db8f6e3813 01410484ecc0d46f1918b30928fa0e4ed99f16a0fb4fde0735e7ade84 16ab9fe423cc5412336376789d172787ec3457eee41c04f4938de5cc1 7b4a10fa336a8d752adfffffffff02 60e31600000000001976a914ab6 8025513c3dbd2f7b92a94e0581f5d50f654e788acd0ef800000000000 1976a9147f9b1a7fb68d60c536c2fd8aeaa53a8f3cc025a888ac 00000000
The Input Serialization
The input serialization contains the following components:
Now can you locate the input of her transaction?
0100000001 186f9f998a5aa6f048e51dd8419a14d8a0f1a8a2836dd73 4d2804fe65fa35779000000008b483045022100884d142d86652a3f47 ba4746ec719bbfbd040a570b1deccbb6498c75c4ae24cb02204b9f039 ff08df09cbe9f6addac960298cad530a863ea8f53982c09db8f6e3813 01410484ecc0d46f1918b30928fa0e4ed99f16a0fb4fde0735e7ade84 16ab9fe423cc5412336376789d172787ec3457eee41c04f4938de5cc1 7b4a10fa336a8d752adfffffffff 0260e31600000000001976a914ab6 8025513c3dbd2f7b92a94e0581f5d50f654e788acd0ef800000000000 1976a9147f9b1a7fb68d60c536c2fd8aeaa53a8f3cc025a888ac 00000000
Alright. So what have we seen so far?
- The outputs of a transaction and the UTXOs.
- The inputs of a transaction.
- How the entire transaction is being serialized.
Now, we know that UTXOs can only be used if they are unlocked. We know that input values have scriptSig which helps unlock them. How do they interact with each other?
Before we get to that though. We should have an idea of how calculations and operations happen in a bitcoin script.
How Does the Script Work?
Before we continue with Script. It will be helpful to understand how a stack-based. Reverse-polish system works.
Simple Addition in a Stack-based Reverse-polish System
As we have said before 3+4 in reverse-polish will look like 34+. Let’s execute the addition operation using a stack.
That’s how a simple addition operation gets done on the stack. Now that this is done. How would this look like if it were a script?
OP_3 OP_4 OP_ADD
Just the appearance changes. The rest of the operation remains the same as shown above. The “OP_” prefix is a signature of the Script language.
If you want a primer on the different Opcodes that are used in a script then click here.
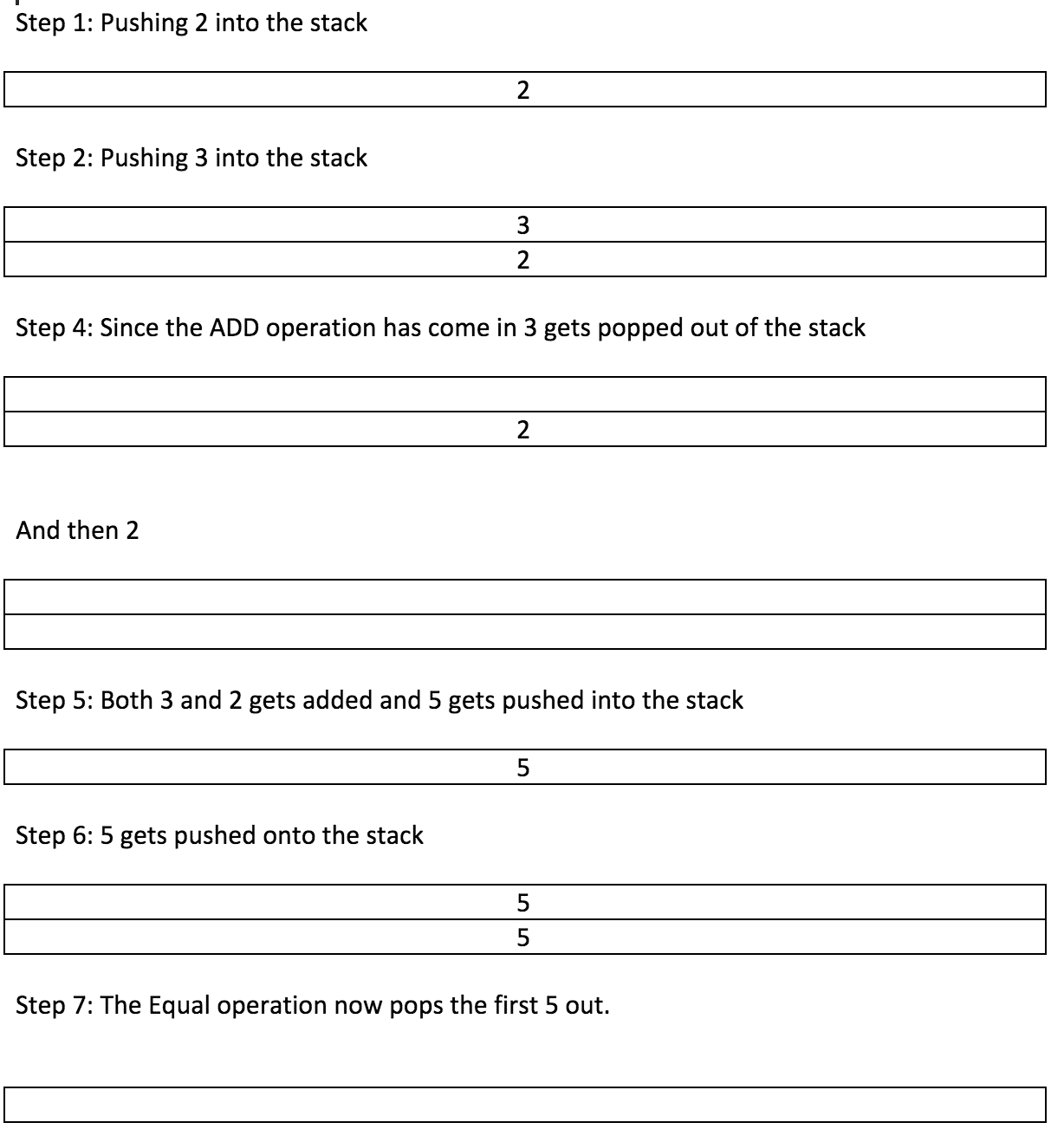
Simple Addition Using Bitcoin Script with a Check
Now suppose we want to do 2+3=5.
In Reverse Polish it will look like 23+5=.
In script notation it will look like this:
OP_2 OP_3 OP_ADD OP_5 OP_EQUAL
Now, what would have happened if we used the postfix VERIFY in EQUAL? Meaning, instead of OP_EQUAL we used OP_EQUALVERIFY?
The moment you add the VERIFY suffix. TRUE or FALSE doesn’t get pushed on the stack, instead. The script continues executing if TRUE or it stops executing if it is FALSE.
This is what happens when you append “VERIFY” to an opcode. Keep this in mind for future examples.
Alright, let’s take one last example.
Simple Duplication in the Script
We are taking this example just to introduce you to an extremely important opcode. DUP aka duplicate.
Let’s, we want to push a number into a stack. Duplicate it. And see if the two numbers are same or not (which it obviously will be).
We are going to use this script:
OP_5 OP_DUP OP_EQUALVERIFY
Alright, now you have an idea of how calculations get processed in bitcoin Script. Let’s continue with our transactions and see how they get executed.
The Game of Locking and Unlocking
Transactions in bitcoin are a constant game of locking and unlocking. The UTXOs are locked up by the scriptPubKey while the inputs of the transaction contain the scriptSig. The idea of scriptPubKey is to offer a cryptographic puzzle which can only be unlocked via the corresponding scriptSig.
So, what exactly happens and how is this game played?
Suppose, Alice wants to send Bob some bitcoin. Bob’s public address is common knowledge and she will send her Bitcoins to Bob’s public address along with a condition. Bob must prove that it is indeed him who is getting the bitcoin.
Now, let’s go back for a bit. And revisit some basic concepts.
Everyone in bitcoin has two keys:
The public key is cryptographically derived from the private key.
Now, in order to get money sent to them. Everyone must have a public address. The public is run through two hashing algorithms. SHA-256 and RIPEMD-160. The reason why we do this is to make sure that you have an extra layer of protection. IF in the case that someone somehow figures out how to generate your private key using your public key (which is infeasible).
Note: The public key first goes through SHA-256 to give a 256-bit output hash. And then that hash is run through RIPEMD-160 which gives a 160-bit output hash. So, the final output is a 160-bit hash.
Alright, so Alice will send the money to Bob’s public address along with a condition that Bob must show a proof. That it is indeed him who have gotten the money.
The proof that Bob uses to unlock the funds is his Digital Signature. Which cryptographically derived from his private key.
Think of the transactions that Alice sends Bob as a locked chest. And Bob’s signature as the passcode.
Now, getting back to our script.
Alice sends Bob an output which has the scriptPubKey. Which includes Bob’s address.
Bob unlocks the input using his signature of scriptSig which includes his signature and his public key.
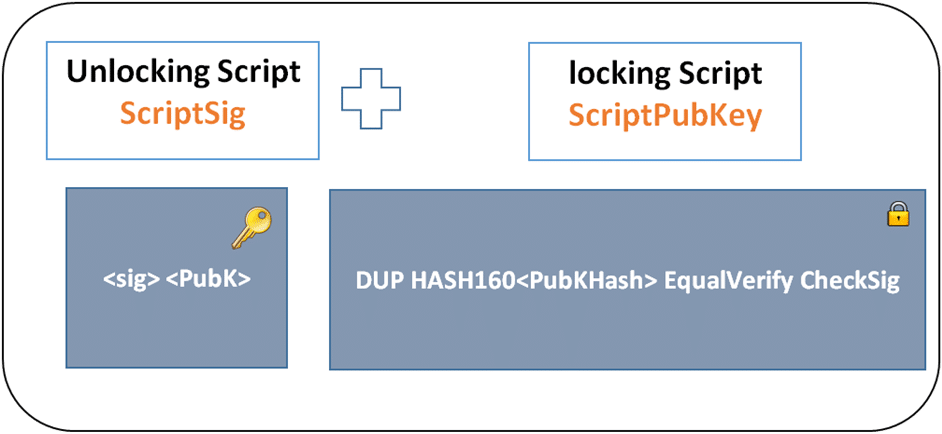
So, how do we represent this in code?
scriptPubKey = OP_DUP OP_HASH160 OP_EQUALVERIFY OP_CHECKSIG.
Note: How OP_HASH160 and OP_CHECKSIG works will be clear to you soon.
In order to unlock the output and use his funds Bob concatenates or kinda joins the scriptSig and the scriptPubKey like this:
Alright, now let’s see how the script works to give poor Bob access to his funds. The script right now looks like this:
OP_DUP OP_HASH160 OP_EQUALVERIFY OP_CHECKSIG.
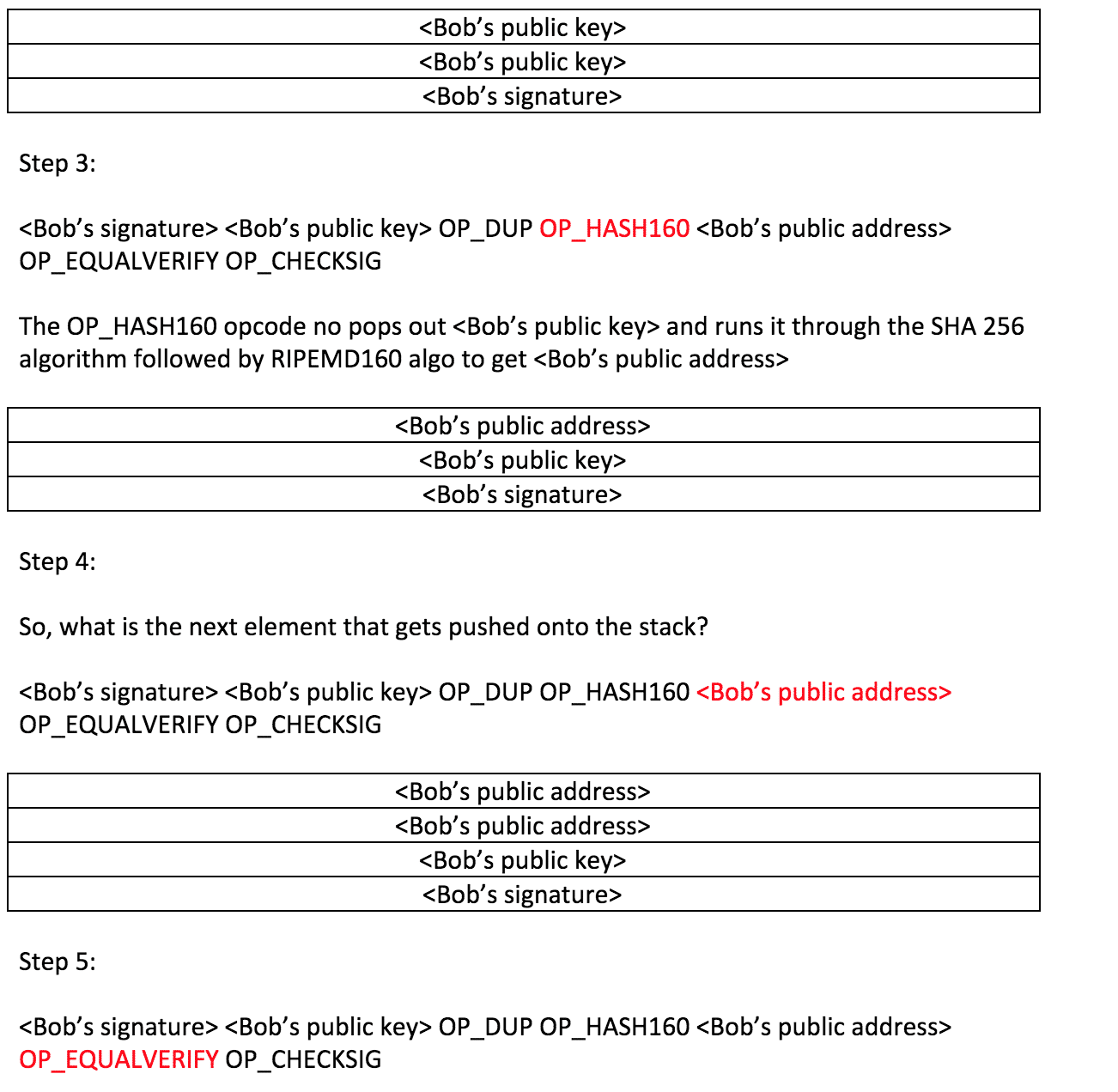
Script Implementation of the Unlocking/Verification Process
Ok, now let’s see how the script implementation of the entire verification/unlocking process works.
Right now, the code looks like this
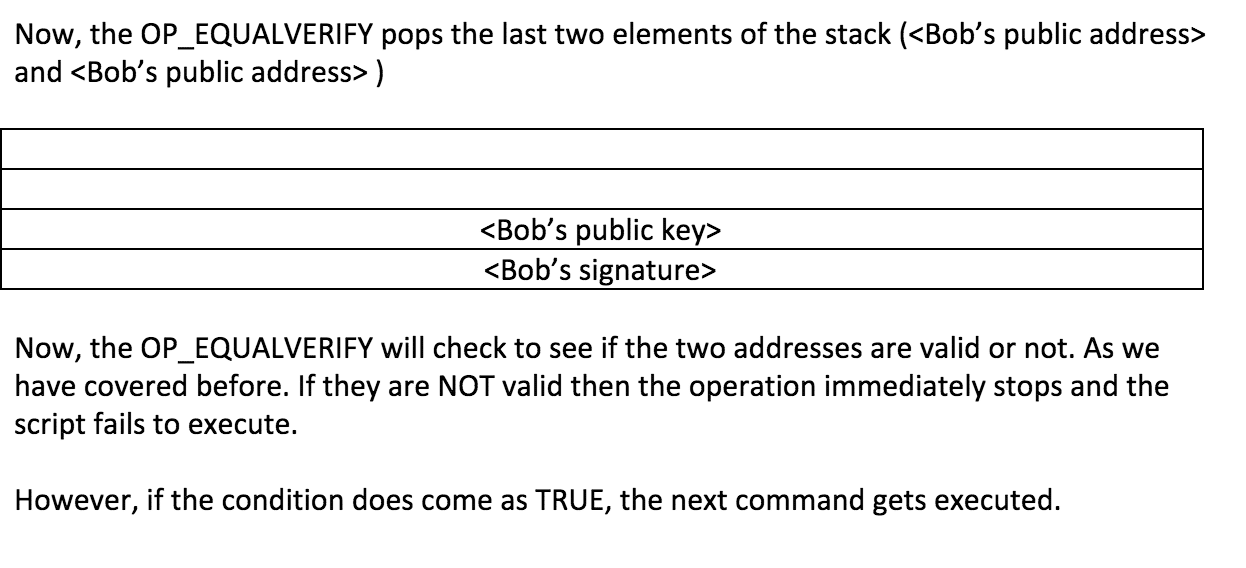
The OP_CHECKSIG pops out and and checks to see their validity to know that they are valid signatures and public addresses.
When this entire process is done. Bob can unlock the transaction and gets access to his funds.
Congratulations! You just went through an entire bitcoin transaction!
What you see here is the most common type of bitcoin transaction: The P2PKH aka The pay to public key hash.
So, what is this mysterious CHECKSIG operator and how does it work? Well, for that we need to look at the cryptography behind bitcoin.
How does CHECKSIG work?
In order to know how CHECKSIG works. We will need to know what a digital signature is. A digital signature is a digital code (generated and authenticated by public key encryption) which is attached to an electronically transmitted document to verify its contents and the sender’s identity.
The digital signature algorithm used by bitcoin is ECDSA or the Elliptical Curve Digital Signature Algorithm.
Elliptical curve cryptography is what is used by bitcoin. Ethereum etc. for their encryption purposes. So what is an elliptical curve? An elliptical curve is any curve that satisfies the following equation:
Where (x,y) is a point on the curve and a and b are constants.
There are infinite curves that you can make. The following is how one of these curves, in general, look like:
Image credit: CSBreakdown youtube channel
What are the properties of an elliptic curve?
- The curve is symmetric across the x axis.
- Any line that goes through 2 points on the curve will intersect the curve on a third point.
- Any tangent on the curve will intersect the curve on one more point.
Performing maths on the curve.
Addition property of the curve
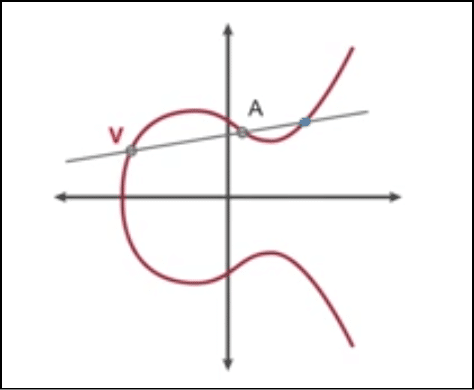
Suppose there are two points on the curve V and A. Let’s trace those on the curve and put a line through them. This will intersect the curve on a third point.
Image credit: CSBreakdown youtube channel
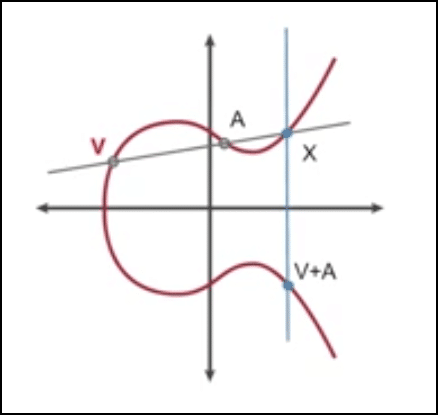
We will call this third point X. And we will reflect it on the curve like this:
Image credit: CSBreakdown youtube channel
The reflection of X is a point which will incidentally be (V+A). This is the additive property of the elliptical curve.
Interesting note. If we add two reflections with each other aka if we were to add X and V+A in the graph above. We will get infinity. The reason for that is that the line through X and (V+A) will intersect the curve at infinity.
Multiplication property of the curve
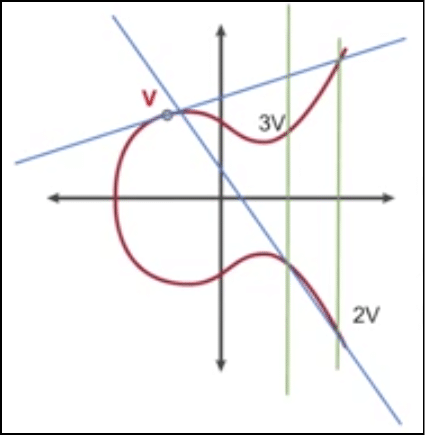
Now, what if we want to add a number to itself? Like suppose we have a point V. What do we do to find 2V? We will run a tangent through V and intersect it at a point in the graph and then find the reflection of the point on the curve. That reflection will be 2V.
Image credit: CSBreakdown youtube channel
This is also the multiplicative property of the graph because we are finding points which are basically the multiplication of an integer with the point itself. Now suppose we want to find 3V. We will join V and 2V and then reflect the point of intersection, like this:
Image credit: CSBreakdown youtube channel
You see how the points cycle across the graph? This is what gives it its security.
Mathematical properties of an elliptical curve
Property #1: The points on the curve form an Abelian group
The properties of the Abelian group are as follows:
- They have an identity.
- They have inverses aka reflections.
- The points are associative meaning for three points A. B and C on the curve: (A+B) + C = A + (B+C).
- The points are closed on the curve.
- The points are commutative meaning for two points A and B. A+B = B+A.
Property #2: Multiplication on the curve is fast
All multiplication done on the curve can be done very fast. Now suppose we have a point P and we want to find 100P. Instead of adding the number to itself 100 times we can do the following:
- Add the point P to itself to get 2P.
- Add 2P and P to get 3P.
- Add 3P to itself to get 6P.
- Add 6P to itself to get 12P.
- Add 12P to itself to get 24P.
- Add 24P and P to get 25P.
- Add 25P to itself to get 50P.
- Add 50P to itself to get 100P.
So, instead of going through 99 steps you cut short the entire thing to just 8 steps.
Property #3: Division on the curve is slow
Whilst multiplication is fast. Division is very slow. Suppose we have Q = nP and we want to find the value of n by dividing Q by P. We can’t really do that. We will have to manually go through the numbers one by one to find a value which satisfies the equation. This makes it very slow. This is called the discrete logarithmic problem and this is what gives the curves its trapdoor function i.e. it is easy to multiply n and P to get Q but given Q and P. It is infeasible to get n.
So how does signature verification work on the elliptical curves?
(Note: This is what specifically happens in bitcoin)
Before we see how the process works let’s check out certain variables and their meaning that we will be using in the following equations.
G will be a constant point on the graph which will be provided by bitcoin.
“k” is a random number which will be generated automatically for every unique signature.
“n” is another constant that will be provided by bitcoin.
Ok, so now let’s see how the maths behind the verification work’s.
Signing a message
Public key Q = dG. (it is impossible to get the private key from Q and G because of division in infeasible).
Now we will multiply the G with the random number “k” and plot that point on the graph. The coordinates of that point are (x,y). i.e. (x,y) = kG
Next, we determine two values r and s such that:
s = (z + rd) k^-1 mod n
The reason why we generate r and s is that these are the coordinates of our signature.
So, we send the point (r,s) for verification.
Verifying a message
The verifiers will conduct a simple equation:
The value of this equation will give us the point (x,y).
Now, the verifiers can simply compare the x coordinates. They don’t have the x coordinate given directly to them by the sender BUT they have the values of r and n.
And as we already know that r = x mod n. And then they can simply solve for x.
If the values of x match out. Then this means that the signature is verified!
Bonus: A deeper look into the maths
Let’s check out the equation that the verifiers will have to do once again:
Step 1: z*s^-1*G + r*s^-1*Q
We know that Q = d*G. Let’s simply substitute the value.
Step 2: z*s^-1*g + r*s^-1*d*G
We can take (z + r*d) common
Step 3: (z + r*d)*s^-1*G
Now remember. We have already established that s = (z+r*d)*k^-1 mod n ,let’s substitute the values here:
Step 4: (z+r*d)*(z+r*d)^-1*k*G
The (z+r*d)*(z+r*d)^-1 cancel each other out and we are left with:
Step 5: k*G which is the co-ordinate (x,y) that the sender originally sent.
What could go wrong in Elliptical curves?
While it goes without saying that elliptical curves are the best mode of cryptography out there. The fact remains that it still has few vulnerabilities:
- What if a wrong curve was chosen? If the curve has a loop in it then there is a possibility that 1001P = P for any point P on the curve.
- A weak curve may be chosen which can be broken into.
It has its weaknesses but they are pretty manageable weaknesses.
END OF PART 1
This is where we are going to end the part 1 of our Bitcoin Script Guide. In part 2 we are going to cover:
- Multisignature Transactions.
- Pay to Script Hash.
- Flow Control.
- Timelocks.
Источник